The term starck torrent has gained steady attention among users searching for peer to peer file sharing platforms in recent years. In 2025, interest in torrent ecosystems continues, but so do questions about safety, legality, and usability. This guide explains starck torrent in plain language, focusing on how it fits into today’s internet landscape, what users should realistically expect, and the risks involved.
This article is written for informational purposes only. It does not promote copyright infringement or illegal activity.
What Is Starck Torrent and Why People Search for It
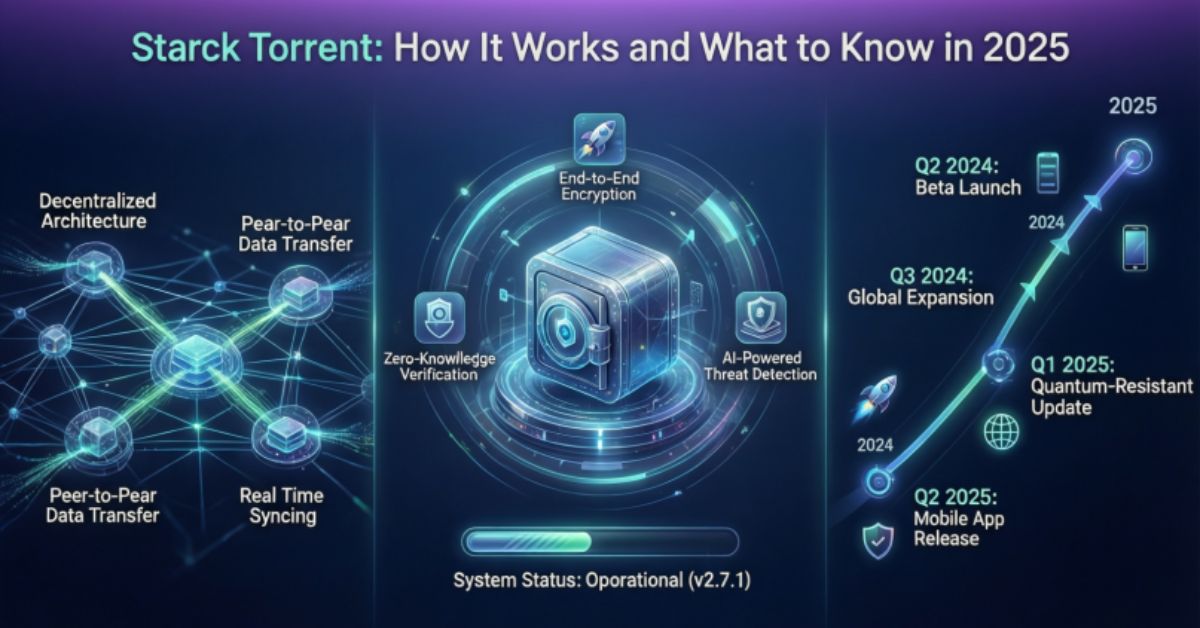
Starck torrent generally refers to a torrent indexing or sharing environment that helps users locate torrent files and magnet links. Torrent platforms do not host files directly. Instead, they act as directories that connect users through peer to peer technology.
The reason starck torrent keeps showing up in search results is simple. Many users want faster access to large files, open source software, public domain media, or community shared content. Torrent technology allows distributed sharing, which reduces the load on any single server.
In the US, awareness around digital rights has increased, and users are more cautious than they were a decade ago. That is why searches often include words like safety, alternatives, and legality alongside starck torrent. People are not just curious about access. They want to understand consequences and risks.
Unlike mainstream streaming platforms, torrent ecosystems are decentralized. That independence is appealing to some users but confusing to others. Understanding what starck torrent actually represents helps users make informed decisions rather than acting on assumptions or outdated information.
How Starck Torrent Works in Simple Terms
At its core, starck torrent relies on BitTorrent protocol fundamentals. Instead of downloading a file from one central source, users download small pieces of the same file from multiple peers.
Here is the basic process explained simply:
- A user searches for a torrent or magnet link
- The torrent file contains metadata, not the actual content
- A torrent client connects the user to other peers
- Pieces of the file are downloaded and shared simultaneously
This system improves speed and resilience, especially for large files. However, it also exposes IP addresses within the swarm. That exposure is one of the biggest concerns in 2025, especially in the United States where copyright monitoring is active.
Starck torrent itself does not control what users download. That distinction matters legally, but it does not eliminate user responsibility. Understanding how peer connections work helps users better assess privacy and security implications.
Key Features Associated With Starck Torrent Platforms
Most environments linked to starck torrent share a common set of features. These features are not unique but influence user experience significantly.
Common features include:
- Search filters based on file size, date, or popularity
- Magnet link support for faster access
- Community comments or ratings
- Categorized listings for software, media, and documents
In 2025, usability matters more than ever. Users expect clean interfaces, fewer intrusive ads, and mobile compatibility. Platforms that fail in these areas tend to lose trust quickly.
However, feature rich interfaces can also hide risks. Fake files, misleading titles, and embedded malware are still present across many torrent ecosystems. A polished design does not guarantee safety.
From an EEAT perspective, platforms that clearly label content types and provide moderation tools are viewed as more credible, even if they operate in a gray area.
Pros and Cons of Using Starck Torrent
Understanding both sides is essential before forming an opinion about starck torrent.
Pros
- Efficient sharing of large files
- Access to open source and public domain content
- No reliance on centralized servers
- Often faster than traditional downloads
Cons
- Legal risks depending on content type
- Exposure of IP addresses
- Malware and fake file threats
- Inconsistent quality control
The biggest mistake users make is assuming all torrents are illegal. That is not accurate. Many developers distribute software updates via torrents. Academic archives also use peer to peer sharing.
The real issue is content choice and user behavior. In the US, downloading copyrighted material without permission can lead to ISP warnings or worse. That risk is not theoretical. It happens regularly.
Legal and Ethical Considerations in the United States
This section matters more than any feature list. Starck torrent itself is not illegal, but how it is used determines legality.
In the United States:
- Copyright law applies regardless of download method
- ISPs monitor traffic patterns
- Repeat infringement can lead to service suspension
Ethically, users should ask a simple question. Do I have the right to access and share this content? If the answer is unclear, caution is the smarter choice.
In 2025, legal alternatives are widely available for most media. Torrent use increasingly makes sense for legitimate use cases like Linux distributions, archival projects, or large datasets.
Responsible use protects both the user and the broader internet ecosystem.
Security Risks and Privacy Concerns to Know
Security remains a major concern around starck torrent. Torrent ecosystems are open by design, which creates vulnerabilities.
Key risks include:
- Malware disguised as popular files
- Tracking by third parties
- Fake torrents seeded to collect data
Many users underestimate how exposed they are. Every peer in a torrent swarm can see IP information. That alone is enough to justify caution.
Using verified torrent clients, keeping systems updated, and avoiding suspicious downloads reduce risk. Still, no method eliminates it entirely.
From a practical standpoint, users who value privacy should reconsider casual torrent use. Convenience should never outweigh security awareness.
Usability and User Experience in 2025
In 2025, usability expectations are high. Platforms associated with starck torrent vary widely in quality.
Good usability includes:
- Clear navigation
- Minimal deceptive ads
- Accurate file descriptions
- Responsive design
Poor usability often signals deeper issues like lack of moderation or outdated infrastructure. Users should pay attention to small details. Broken pages, misleading buttons, and aggressive popups usually indicate higher risk.
Some tech publications, including articles cited on https://usmagazineblog.com/, have highlighted how usability directly impacts trust in online platforms. That insight applies here as well.
A platform that respects users tends to be transparent about limitations and risks.
Starck Torrent Compared to Other Torrent Options
Below is a simplified comparison table to put starck torrent in context.
| Feature | Starck Torrent | Public Torrent Indexes | Private Trackers |
|---|---|---|---|
| Accessibility | High | High | Limited |
| Moderation | Low to Medium | Low | High |
| Privacy | Limited | Limited | Better |
| Content Quality | Mixed | Mixed | Generally Higher |
This comparison highlights a tradeoff. Open access improves reach but reduces control. Private systems offer better quality but require invitations and rules.
Users should decide based on priorities, not hype.
Alternatives to Starck Torrent for Legitimate Use
Not all file sharing needs torrents. Depending on goals, alternatives may offer better outcomes.
Legitimate options include:
- Direct downloads from official sites
- Cloud based file sharing
- Open repositories for software and research
For many users, torrents are a habit rather than a necessity. Re evaluating that habit in 2025 often leads to safer and more efficient choices.
Starck torrent may still have a place, but it is no longer the default solution it once was.
Best Practices for Responsible Use
If users choose to interact with starck torrent, responsibility matters.
Key practices include:
- Stick to legal content
- Verify file sources
- Avoid unknown executables
- Stay informed about local laws
These steps do not eliminate risk, but they reduce it. The goal is informed decision making, not blind avoidance or blind trust.
Key Takeaways
- Starck torrent refers to a torrent based sharing environment, not a file host
- Torrent technology is legal, misuse is not
- Security and privacy risks remain significant in 2025
- Usability varies widely across platforms
- Legitimate alternatives are often safer and simpler
Conclusion
Starck torrent sits at the intersection of convenience, risk, and responsibility. Torrent technology itself is neutral, but outcomes depend entirely on how it is used. In 2025, users have more legal options, better information, and higher expectations for safety.
Understanding how starck torrent works, what risks exist, and where boundaries lie allows users to make informed choices. That awareness matters more than speed or access. When users prioritize legality and security, they protect not only themselves but the broader digital ecosystem as well.
Frequently Asked Questions
Is starck torrent a hosting website?
No, it indexes torrent metadata rather than storing files.
Can starck torrent be used for open source projects?
Yes, many open source distributions use torrent technology legally.
Does using starck torrent automatically break US law?
No, legality depends on the content being downloaded or shared.
Are torrent clients the same as starck torrent?
No, clients download files while starck torrent refers to discovery platforms.
Is torrenting still relevant in 2025?
Yes, but mostly for niche and legitimate use cases.